CVE-2025-54253
Adobe Experience Manager Forms Code Execution Vulnerability - [Actively Exploited]
Description
Adobe Experience Manager versions 6.5.23 and earlier are affected by a Misconfiguration vulnerability that could result in arbitrary code execution. An attacker could leverage this vulnerability to bypass security mechanisms and execute code. Exploitation of this issue does not require user interaction and scope is changed.
INFO
Published Date :
Aug. 5, 2025, 5:15 p.m.
Last Modified :
Oct. 23, 2025, 2:51 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CISA KEV (Known Exploited Vulnerabilities)
For the benefit of the cybersecurity community and network defenders—and to help every organization better manage vulnerabilities and keep pace with threat activity—CISA maintains the authoritative source of vulnerabilities that have been exploited in the wild.
Adobe Experience Manager Forms in JEE contains an unspecified vulnerability that allows for arbitrary code execution.
Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable.
Unknown
https://helpx.adobe.com/security/products/aem-forms/apsb25-82.html ; https://nvd.nist.gov/vuln/detail/CVE-2025-54253
Affected Products
The following products are affected by CVE-2025-54253
vulnerability.
Even if cvefeed.io is aware of the exact versions of the
products
that
are
affected, the information is not represented in the table below.
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | CRITICAL | [email protected] |
Solution
- Update Adobe Experience Manager to version 6.5.24 or later.
- Review Adobe's security advisories for specific configuration guidance.
- Apply security hardening best practices for AEM deployments.
Public PoC/Exploit Available at Github
CVE-2025-54253 has a 12 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2025-54253.
| URL | Resource |
|---|---|
| https://helpx.adobe.com/security/products/aem-forms/apsb25-82.html | Vendor Advisory |
| https://slcyber.io/assetnote-security-research-center/struts-devmode-in-2025-critical-pre-auth-vulnerabilities-in-adobe-experience-manager-forms/ | Exploit Third Party Advisory |
| https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-54253 | Third Party Advisory US Government Resource |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2025-54253 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2025-54253
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
CVE-2025-54253 | CVE-2025-54254 | Adobe Experience Manager Forms XXE → RCE Framework
Python
Public exploit for CVE-2025-54253
zero-day
Breaking down CVE-2025-54253 — an Adobe AEM-Forms exploit path from XXE to full remote code execution and its real-world impact.
adobe cve exploit rce xxe cybersecurity
cve-2025-54253
آسیبپذیری بحرانی با شناسه CVE-2025-54253 در محصول Adobe Experience Manager Forms (JEE) شناسایی شده است
🚨 Demonstrate CVE-2025-54253, a critical OGNL injection vulnerability in Adobe AEM Forms, for educational and research purposes.
aem-forms-on-jee curl cve-2025-54253 cybersecurity ethical-hacking exploit local-testing offensive-security ognl-injection-vulnerability penetration-testing poc proof-of-concept rce red-team remote-code-execution vmware-lab vulnerability-research
Python
🐙 CVE-2025-54253 exploit demo for Adobe AEM Forms on JEE: OGNL injection to RCE with PoC, Python 3.10 exploit code, reproducer and mitigation guidance.
aem-forms-on-jee curl cve-2025-54253 cybersecurity ethical-hacking exploit local-testing offensive-security ognl-injection-vulnerability penetration-testing poc proof-of-concept rce red-team remote-code-execution vmware-lab vulnerability-research
Python
None
Simulated PoC for CVE-2025-54253: Adobe AEM OGNL Injection Vulnerability
adobe-aem curl cybersecurity ethical-hacking exploit infosec local-testing offensive-security ognl-injection-vulnerability penetration-testing poc proof-of-concept rce red-team remote-code-execution vulnerability-research aem-forms-on-jee cve-2025-54253 vmware-lab
Python
CVE-2025-54253
监控Github最新网络安全相关的仓库...
cve cybersecurity github spider
Shell Python Nix
A repo for output of an intrusion prediction project
Jupyter Notebook Python Standard ML
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2025-54253 vulnerability anywhere in the article.
-
Daily CyberSecurity
Critical Triofox Zero-Day (CVE-2025-12480) Under Active Exploit: Host Header Bypass Allows Unauthenticated Admin Takeover
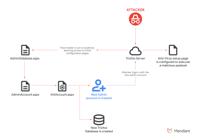
CVE-2025-12480 exploitation chain | Image: Mandiant Threat Defense Researchers at Mandiant Threat Defense, part of Google Cloud Security Operations, have revealed that a critical unauthenticated acces ... Read more
-
Daily CyberSecurity
SuiteCRM SQL Injection Flaws (CVE-2025-64492, CVE-2025-64493) Expose Customer Data
The maintainers of SuiteCRM, the popular open-source customer relationship management (CRM) platform, have released an urgent security update addressing two significant SQL injection vulnerabilities t ... Read more

-
Daily CyberSecurity
Critical Devolutions Server Flaw (CVE-2025-12485, CVSS 9.4) Allows User Impersonation via Pre-MFA Cookie Hijacking
Devolutions, a leading provider of privileged access management (PAM) and remote connection solutions, has released an urgent security advisory addressing two serious vulnerabilities in its Devolution ... Read more

-
Daily CyberSecurity
Critical WatchGuard Firebox Flaw (CVE-2025-59396, CVSS 9.8) Allows Unauthenticated Admin SSH Takeover via Default Credentials
A critical configuration flaw (CVE-2025-59396) has been discovered in WatchGuard Firebox devices, allowing remote attackers to gain unauthorized administrative access via SSH using default credentials ... Read more

-
Daily CyberSecurity
Critical GE Vernova ICS Flaw (CVE-2025-3222, CVSS 9.3) Allows Authentication Bypass in Smallworld Master File Server
GE Vernova’s Electrification Software division has released a critical security advisory addressing a high-severity authentication vulnerability (CVE-2025-3222) in its Smallworld Master File Server (S ... Read more
-
Daily CyberSecurity
Critical Calibre Flaw (CVE-2025-64486, CVSS 9.3) Allows RCE via Malicious FB2 E-book
A critical vulnerability in Calibre, the popular cross-platform e-book manager, allows arbitrary code execution when an attacker supplies a malicious FictionBook (FB2) file. Tracked as CVE-2025-64486 ... Read more

-
Daily CyberSecurity
Touchscreen MacBook Pro & Foldable iPhone: Apple’s “Most Pivotal Year Yet” Revealed
In addition to the upcoming satellite features for the iPhone, Bloomberg News has outlined Apple’s ambitious 2026 product roadmap, describing it as “the company’s most pivotal year yet.”According to M ... Read more

-
Daily CyberSecurity
Zero-Click Samsung Zero-Day (CVE-2025-21042) Delivered LANDFALL Spyware Via Malicious DNG Images
Researchers from Unit 42, the threat intelligence team at Palo Alto Networks, have discovered a previously unknown Android spyware family dubbed LANDFALL, which leveraged a zero-day vulnerability (CVE ... Read more

-
Daily CyberSecurity
CVE-2025-64439: RCE Flaw Detected in LangGraph: Agent Orchestration Framework at Risk
The LangGraph project, a powerful, low-level orchestration framework trusted by major tech companies for building stateful AI agents, has issued a high-severity security advisory for a Remote Code Exe ... Read more

-
Daily CyberSecurity
High-Severity Elastic Defend Flaw (CVE-2025-37735) Allows Local Attackers to Delete Arbitrary Files as SYSTEM
Elastic has released security updates to address a serious flaw in Elastic Defend, its endpoint protection component within the Elastic Security suite. Tracked as CVE-2025-37735, the vulnerability is ... Read more

-
Daily CyberSecurity
China APT Infiltrates US Policy Nonprofit in Months-Long Espionage Campaign Using DLL Sideloading
A new investigation by the Broadcom Threat Hunter Team has uncovered a China-linked cyber espionage campaign that infiltrated a U.S.-based nonprofit organization involved in influencing U.S. governmen ... Read more
-
Daily CyberSecurity
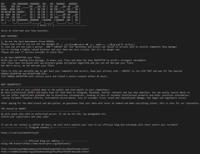
MSP Nightmare: Medusa & DragonForce Exploit SimpleHelp RMM Flaws for SYSTEM Access
Image: Zensec A new report from Zensec has exposed a critical vulnerability in the IT supply chain, detailing how two major Ransomware-as-a-Service (RaaS) groups, Medusa and DragonForce, are actively ... Read more

-
Daily CyberSecurity
PoC Exploit Released for CVE-2025-55680 – Windows Cloud Files Mini Filter Driver Elevation of Privilege Flaw
Security researchers from TyphoonPWN, the Windows PE Winner team, in collaboration with SSD Secure Disclosure, have uncovered a time-of-check to time-of-use (TOCTOU) race condition affecting the Windo ... Read more

-
Daily CyberSecurity
Denmark Moves to Ban Social Media for Under-15s in World-Leading Digital Crackdown
The Danish government has recently announced that members of parliament across the political spectrum—from left to center to right—have reached an agreement to introduce legislation banning anyone und ... Read more

-
Daily CyberSecurity
OCI Fixes Container Escape Vulnerabilities in runc (CVE-2025-31133, CVE-2025-52565, CVE-2025-52881)
The Open Container Initiative (OCI) has released security updates to address three high-severity vulnerabilities affecting its container runtime runc, including flaws that could lead to container esca ... Read more
-
Daily CyberSecurity
High-Severity Cisco ISE Flaw (CVE-2025-20343) Allows Unauthenticated DoS via Crafted RADIUS Requests
Cisco has released a security update to address a high-severity vulnerability (CVE-2025-20343, CVSS 8.6) affecting its Identity Services Engine (ISE) — a core network access control platform used by e ... Read more
-
Daily CyberSecurity
Amazon Fixes High-Severity Authentication Token Exposure in WorkSpaces Client for Linux (CVE-2025-12779)
Amazon has released a security update for the WorkSpaces client for Linux, addressing a high-severity vulnerability (CVE-2025-12779) that could allow local users to extract valid authentication tokens ... Read more

-
Daily CyberSecurity
Critical Cisco CCX RCE Flaws (CVSS 9.8) Allow Unauthenticated Root Access via Java RMI and CCX Editor
Cisco has released urgent security updates to address two critical vulnerabilities in its Unified Contact Center Express (Unified CCX) software, which could allow unauthenticated remote attackers to e ... Read more

-
Daily CyberSecurity
Django Team Patches High-Severity SQL Injection Flaw (CVE-2025-64459) and DoS Bug (CVE-2025-64458) in Latest Security Update
The Django Software Foundation (DSF) has released new security updates for multiple branches of the Django web framework, addressing two vulnerabilities — including a high-severity SQL injection flaw ... Read more

-
Daily CyberSecurity
CISA Warns: Critical VizAir Flaws (CVSS 10.0) Expose Airport Weather Systems to Unauthenticated Manipulation
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical advisory detailing three vulnerabilities in the Radiometrics VizAir aviation weather monitoring system, warning that e ... Read more
The following table lists the changes that have been made to the
CVE-2025-54253 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
Modified Analysis by [email protected]
Oct. 23, 2025
Action Type Old Value New Value Added Reference Type CISA-ADP: https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-54253 Types: Third Party Advisory, US Government Resource -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-54253 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Removed Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-54253 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2025-54253 -
Modified Analysis by [email protected]
Oct. 17, 2025
Action Type Old Value New Value Removed CWE NVD-CWE-noinfo -
CVE Modified by [email protected]
Oct. 16, 2025
Action Type Old Value New Value Added CWE CWE-863 Removed CWE CWE-16 -
CVE CISA KEV Update by 9119a7d8-5eab-497f-8521-727c672e3725
Oct. 16, 2025
Action Type Old Value New Value Added Date Added 2025-10-15 Added Due Date 2025-11-05 Added Vulnerability Name Adobe Experience Manager Forms Code Execution Vulnerability Added Required Action Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable. -
Initial Analysis by [email protected]
Aug. 13, 2025
Action Type Old Value New Value Added CWE NVD-CWE-noinfo Added CPE Configuration OR *cpe:2.3:a:adobe:experience_manager_forms:*:*:*:*:*:*:*:* versions up to (including) 6.5.23.0 Added Reference Type Adobe Systems Incorporated: https://helpx.adobe.com/security/products/aem-forms/apsb25-82.html Types: Vendor Advisory Added Reference Type CISA-ADP: https://slcyber.io/assetnote-security-research-center/struts-devmode-in-2025-critical-pre-auth-vulnerabilities-in-adobe-experience-manager-forms/ Types: Exploit, Third Party Advisory -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Aug. 06, 2025
Action Type Old Value New Value Added Reference https://slcyber.io/assetnote-security-research-center/struts-devmode-in-2025-critical-pre-auth-vulnerabilities-in-adobe-experience-manager-forms/ -
New CVE Received by [email protected]
Aug. 05, 2025
Action Type Old Value New Value Added Description Adobe Experience Manager versions 6.5.23 and earlier are affected by a Misconfiguration vulnerability that could result in arbitrary code execution. An attacker could leverage this vulnerability to bypass security mechanisms and execute code. Exploitation of this issue does not require user interaction and scope is changed. Added CVSS V3.1 AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H Added CWE CWE-16 Added Reference https://helpx.adobe.com/security/products/aem-forms/apsb25-82.html